Luna Moth extortion hackers pose as IT help desks to breach US firms

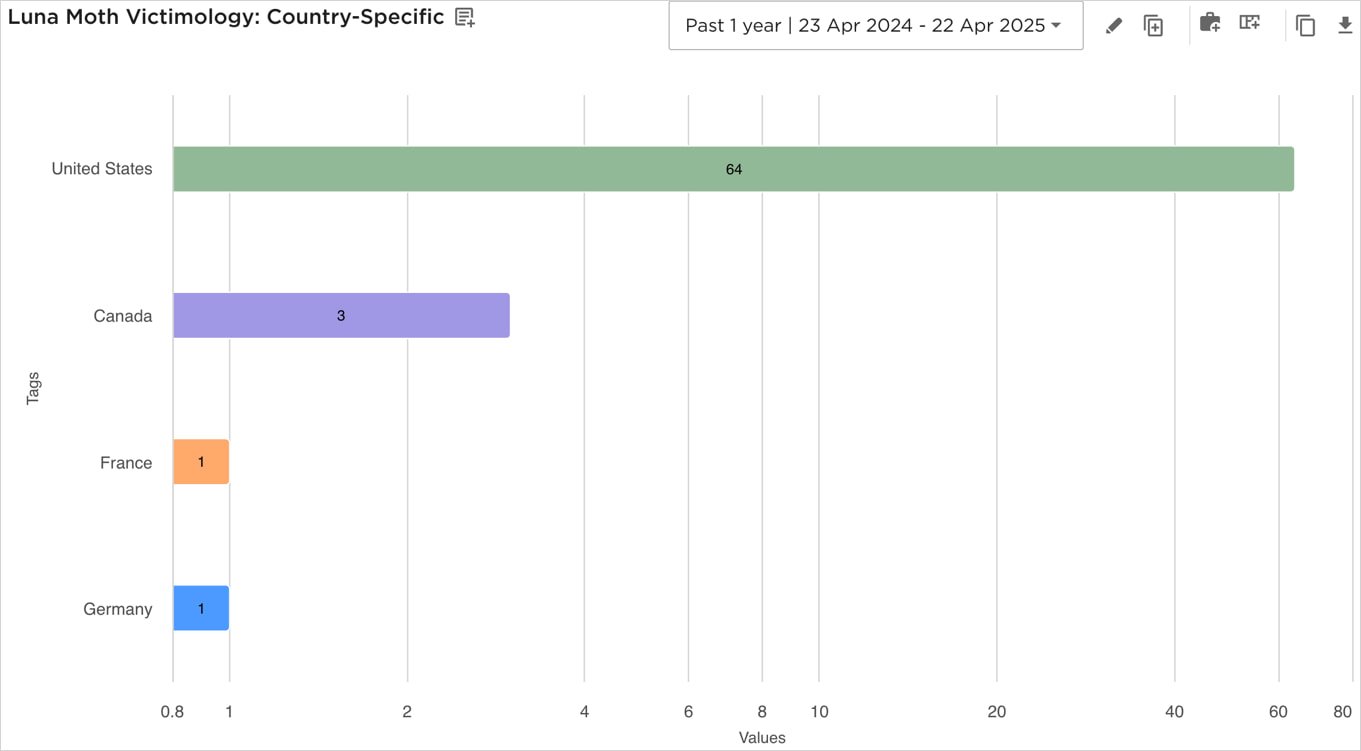
The data-theft extortion group known as Luna Moth, aka Silent Ransom Group, has ramped up callback phishing campaigns in attacks on legal and financial institutions in the United States.
According to EclecticIQ researcher Arda Büyükkaya, the ultimate goal of these attacks is data theft and extortion.
Luna Moth, known internally as Silent Ransom Group, are threat actors who previously conducted BazarCall campaigns as a way to gain initial access to corporate networks for Ryuk, and later, Conti ransomware attacks.
In March 2022, as Conti started to shut down, the BazarCall threat actors separated from the Conti syndicate and formed a new operation called Silent Ransom Group (SRG).
Luna Moths’s latest attacks involve impersonating IT support through email, fake sites, and phone calls, and rely solely on social engineering and deception, with no ransomware deployment seen in any of the cases.
“As of March 2025, EclecticIQ assesses with high confidence that Luna Moth has likely registered at least 37 domains through GoDaddy to support its callback-phishing campaigns,” reads the EclecticIQ report.
“Most of these domains impersonate IT helpdesk or support portals for major U.S. law firms and financial services firms, using typosquatted patterns.”
Source: EclecticIQ
The latest activity spotted by EclecticIQ starts in March 2025, targeting U.S.-based organizations with malicious emails that contain fake helpdesk numbers recipients are urged to call to resolve non-existent problems.
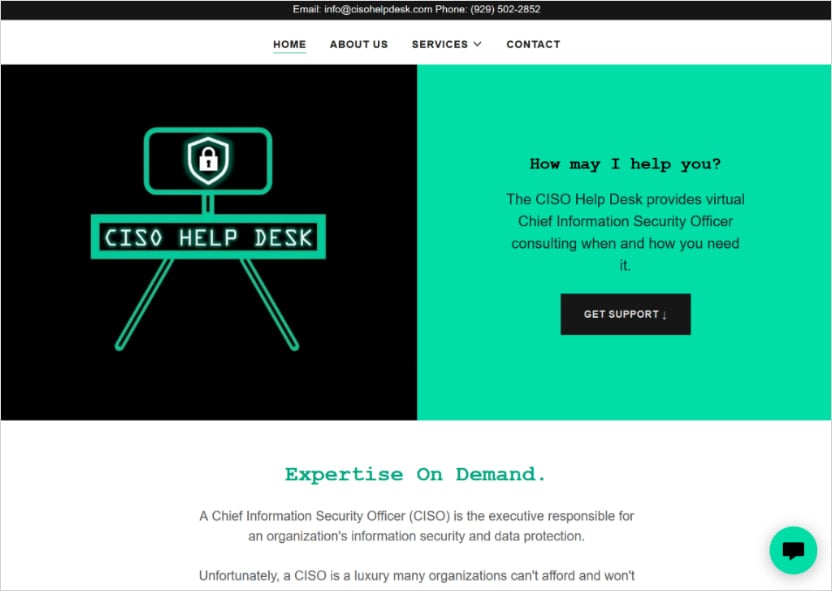
A Luna Moth operator answers the call, impersonating IT staff, and convinces the victim to install remote monitoring & management (RMM) software from fake IT help desk sites that gives the attackers remote access to their machine.
The fake help desk sites utilize domain names that follow naming patterns like [company_name]-helpdesk.com and [company_name]helpdesk.com.
Source: EclecticIQ
Some tools abused in these attacks are Syncro, SuperOps, Zoho Assist, Atera, AnyDesk, and Splashtop. These are legitimate, digitally signed tools, so they’re unlikely to trigger any warnings for the victim.
Once the RMM tool is installed, the attacker has hands-on keyboard access, allowing them to spread to other devices and search local files and shared drives for sensitive data.
Having located valuable files, they exfiltrate them to attacker-controlled infrastructure using WinSCP (via SFTP) or Rclone (cloud syncing).
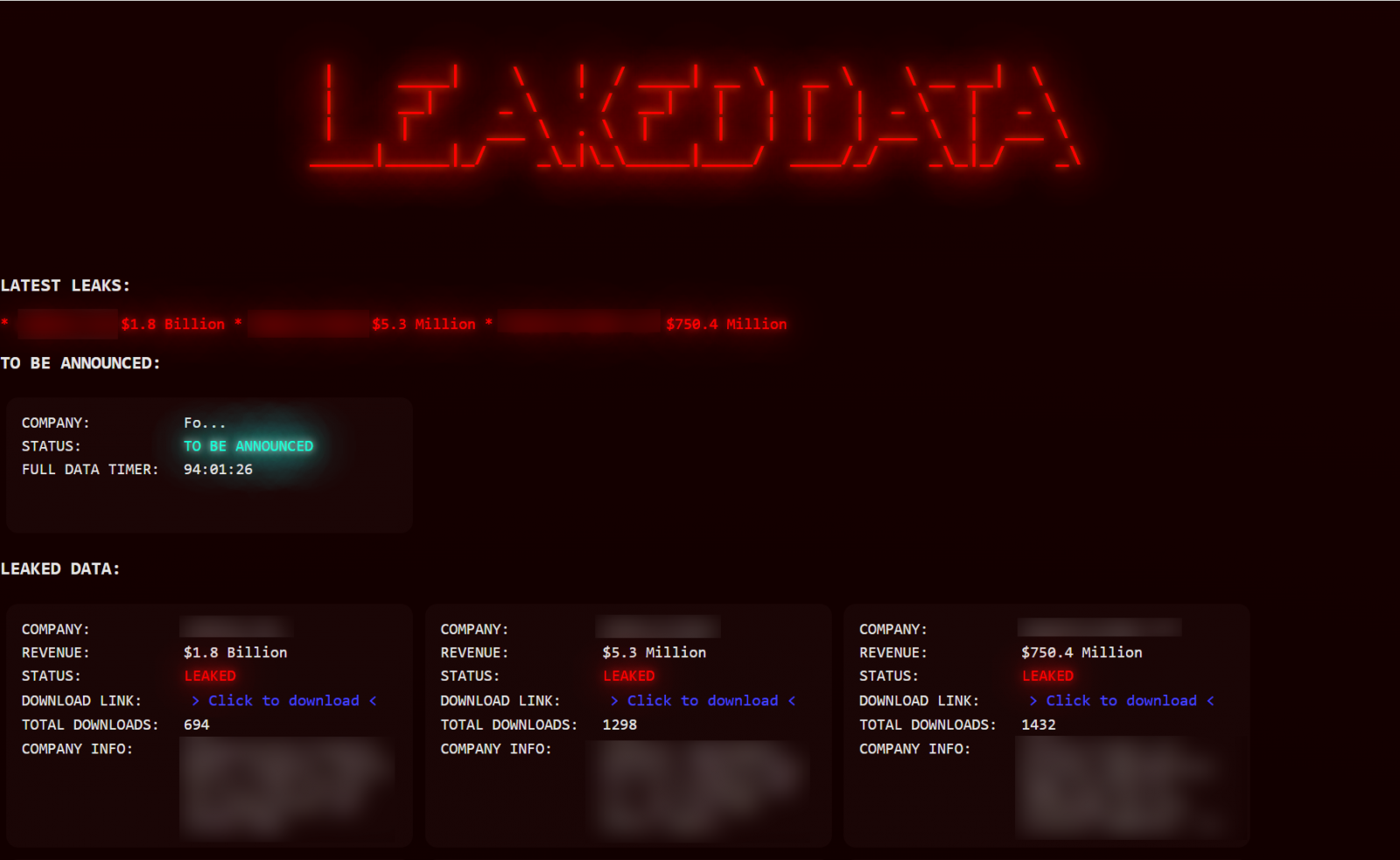
After the data is stolen, Luna Moth contacts the victimized organization and threatens to leak it publicly on its clearweb domain unless they pay a ransom. The ransom amount varies per victim, ranging from one to eight million USD.
Source: BleepingComputer
Büyükkaya comments on the stealth of these attacks, noting that they involve no malware, malicious attachments, or links to malware-ridden sites. The victims simply install an RMM tool themselves, thinking they are receiving help desk support.
As the enterprise commonly uses these RMM tools, they are not flagged by security software as malicious and are allowed to run.
Indicators of compromise (IoCs), including IP addresses and phishing domains that should be added to a blocklist, are available at the bottom of EclecticIQ’s report.
Apart from the domains, it is also recommended to consider restricting the execution of RMM tools that are not used in an organization’s environment.
Source link












